
Several years ago, we wrote about a new feature (new in version 4.0.52!) that allowed for more secure passwords in HIFIS, with more options for customizing.
Internet security has evolved, so we thought it was time to revisit our old discussion. HIFIS has several features that allow you to configure some things, but how should you configure them?
Password Expiry
One thing that has been examined recently is policies that force a user to create a new password every so often (typically 90 days). As of 2019, Microsoft is no longer recommending password expiry as a default setting. Why is this? Because it's outdated. First, password expiry policies were created back in the olden days when it might take 90 days to hack a password, so resetting a password every 90 days made good sense. However, these days a typical password can be hacked in mere hours, not months. So resetting a password for this reason is somewhat irrelevant.
In addition, there are reasons why password expiry policies REDUCE security. Why? Because it's harder for a user to remember a new, strong password every three months, so they tend to fall back on easy-to-remember (and therefore easy-to-hack) passwords. Or they add an incremental number each time they are forced to change their password. If my password is ilovefluffy and I'm forced to change it, ilovefluffy2 isn't really any more secure than ilovefluffy, but it technically meets the requirements for a new password. Or, if you're the sort of person who does like strong passwords, like 72Nje9@nw8, you're very unlikely to remember the string of random characters if it changes every three months. So what do you do? Tell your browser to save it, or write it on a sticky note. These are also not particularly secure practices.
So the experts are saying that you shouldn't have a password expiry policy... most of the time. What they're actually saying is IF you have other strong security practices in place, you shouldn't expire your passwords.
Password Complexity
A second thing you can do to make your accounts more secure is to increase the complexity of your passwords is to require special characters. This is pretty common, right? How many times have you created an online account and set up a password that says, "you need at least 1 upper case letter, 1 number, and one special character"?
Well, turns out this is also not recommended. Why? Because it's harder for users to remember these crazy passwords (and annoying to find a password that meets the requirements), but it's not particularly more secure. P4$sw0Rd and Password!1 are not that much more secure of a password than password, and they can be a lot harder to remember: was the o the number zero or a capital O?
Okay, so what's an admin to do? If we shouldn't expire passwords, nor should we enforce password complexity?
Password Length
Okay, enough messing around. One of the things that IS recommended is longer password length. Microsoft recommends 8-character minimum length requirement, but they also have some other tools available at their disposal. However, most sources suggest that the best practice is to say, hey, don't use a passWORD, use a passPHRASE.
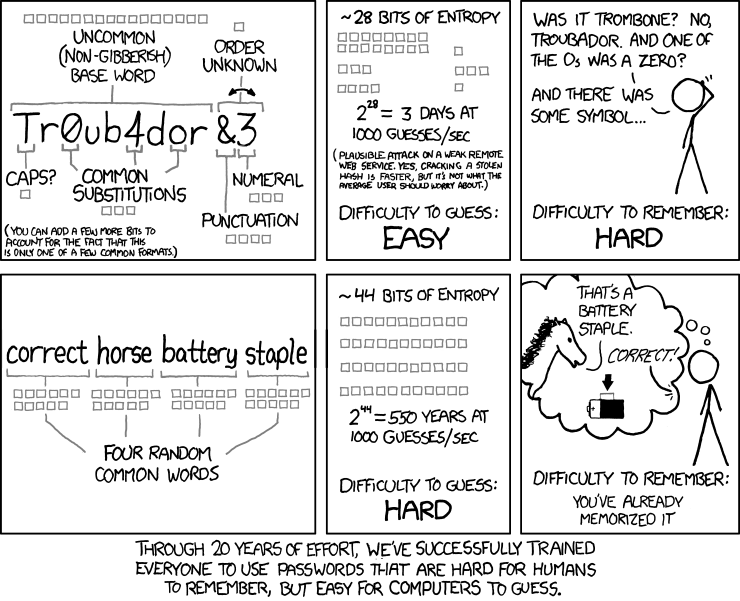
Experts recommend that a password should be permitted to be up to at least 64 characters long, and include spaces and emojis. HIFIS does actually let you do this! You can include spaces and emojis in your password.
Then, of course, there are passwords like this:
The ❄️ 🌟 🔦 ⚪ on the mountain 🌙 🌠. 🙅🏻 a👣 to 🐝 👀. A 🏰 of 😢, and it 👀 like☝️️ the 👑. The 💨 is 🐺 like this 🌀 ❄️ ☔️ 🏠. 🙅🏻 keep it in, ☁️ 💡 ☝️️ tried.
If someone really wants to have a password that's an emoji representation of the first verse of "Let It Go" from Frozen, good on 'em!
https://ldapwiki.com/wiki/Password%20Character%20Composition
Many experts suggest that 8-character passwords are too easy to crack and that "length, not complexity, is the new entropy." Some say we should be encouraging passPHRASEs by upping the minimum password length to something more like 16 characters. Yes, 16. But Microsoft disagrees, saying that this can result in undesirable, repeated passwords such as passwordpassword. This one is a bit of a toss-up, and should really be balanced against all the other tools you have in play.
Multi-Factor Authentication
Finally, the last thing that we can enforce that's considered a good practice is multi-factor (or two-factor) authentication, also known as MFA or 2FA. HIFIS allows for integration with Twilio, which does have an associated cost. But if you're okay with paying for it and managing the logistics, 2FA is widely accepted to be an industry best practice.
Other Things You Can Do
There are a few other best practices that you can do, but none of the remainder of this list are well integrated with HIFIS, so it's on you. You can:
-
Obey the rule of least privilege and don't give users more access than they need
-
Monitor for active accounts that aren't regularly in use
-
Train staff to have a unique password for work than for their personal accounts
Here are some things that HIFIS doesn't really do:
-
Ban common passwords or easy-to-guess ones
-
Bulk reset passwords and require a new password after a suspected breach
-
Keep a password history and preventing password reuse
-
Prevent a user from creating a password that matches their personal data, like their name or birthday or username
Conclusion
While we don't pretend to be the world's leading expert on password security by any stretch of the imagination, we've consulted with experts in the field and have come up with our own policies for HIFIS passwords, and they include: no complexity rules, no password expiry, long minimum password length, and two-factor authentication.

Comments